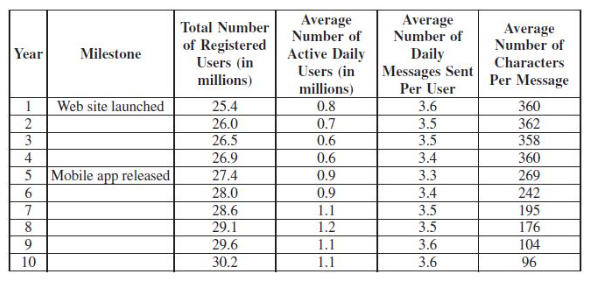
A group of environmental scientists is developing a simulation to predict the spread of wildfires in a forest. The model includes input variables such as wind speed, temperature, humidity, vegetation type, and elevation. The simulation is taking too long to run, so the scientists remove elevation and vegetation type from the model.